Offline
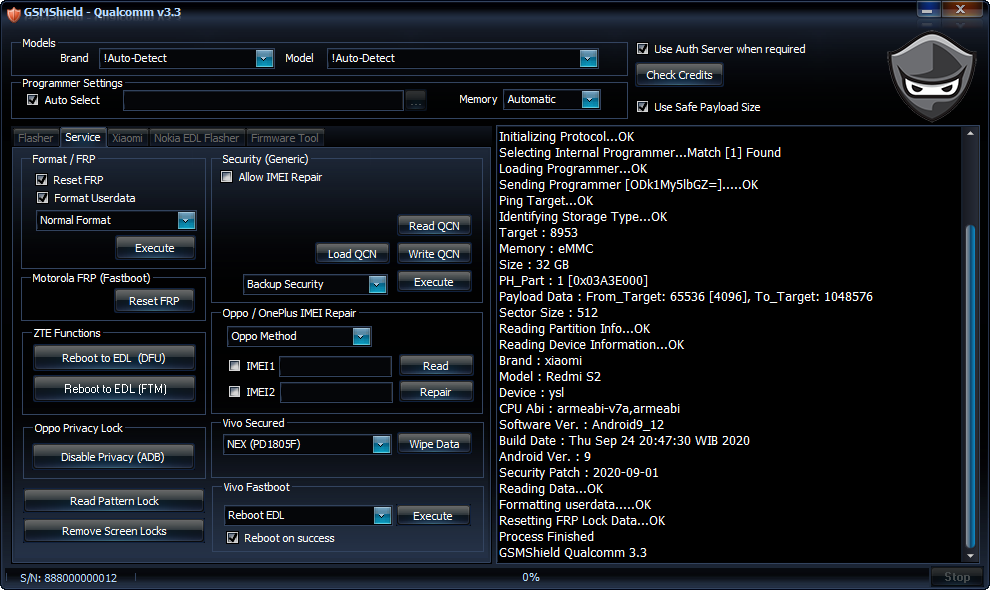
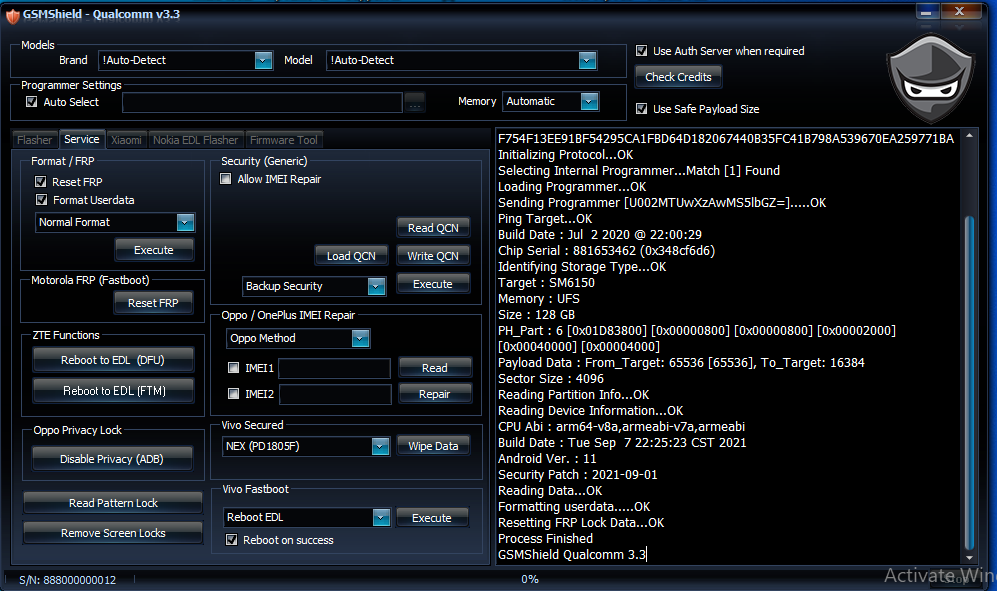
condor pelma p6 -PGN517 flash done
[I]condor pelma p6 -PGN517 flash done[/I]
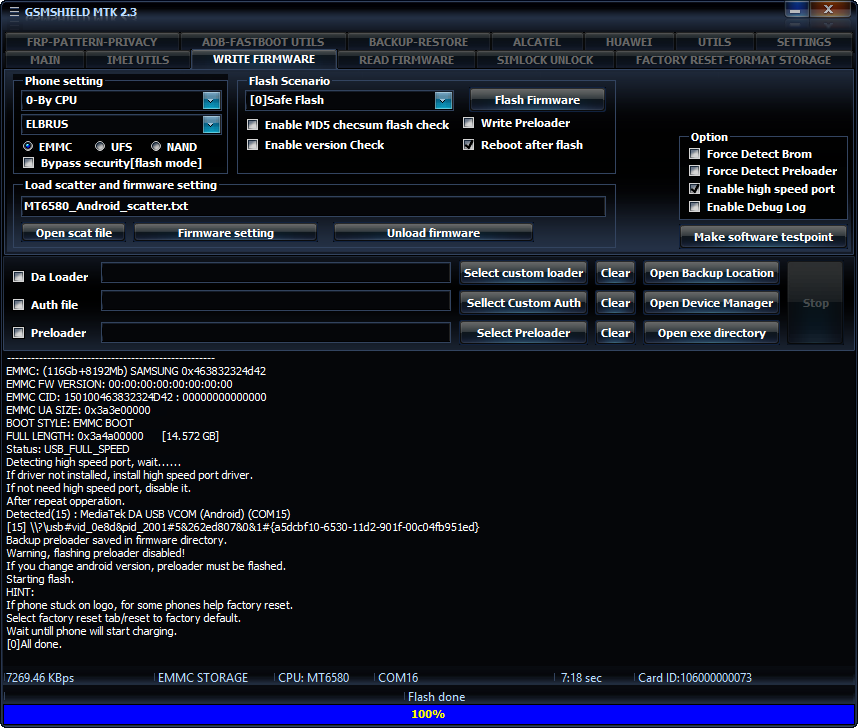
[I]condor pelma p6 -PGN517 flash done[/I]





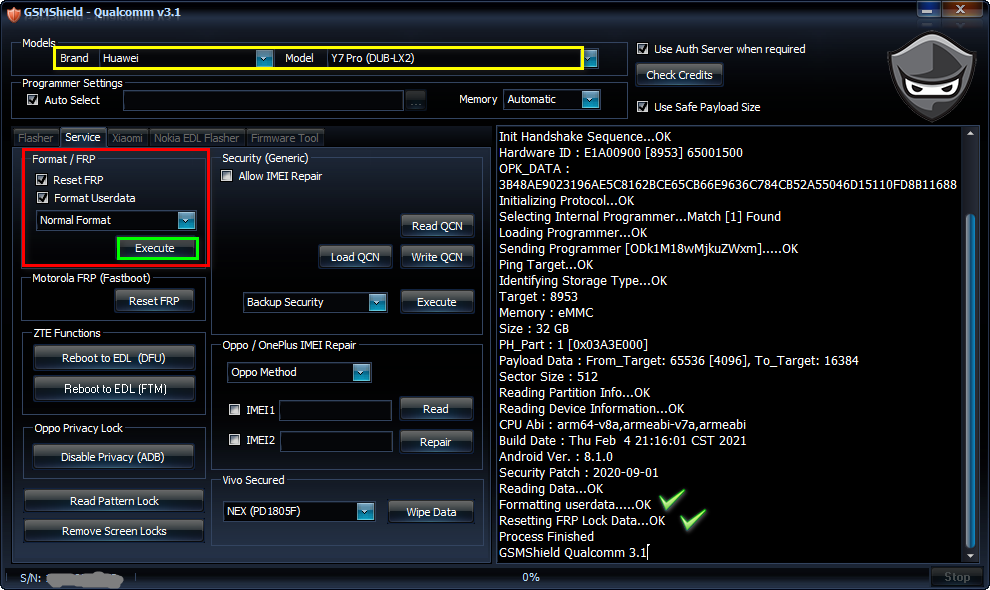
Vivo Y81i vivo 1812 Format Done Easily By Gsm Shield Box
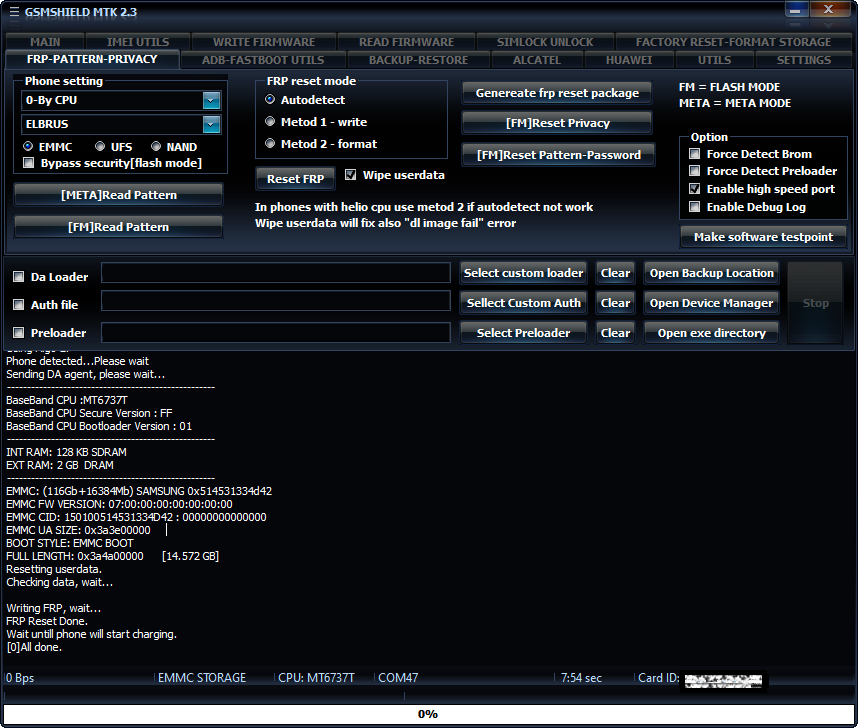
Action : Format UserData.
Selected 0-By CPU:AUTO
Exe version: GSMSHIELD MTK 2.5
Phone must be off with battery inside.
Battery must be charged
Please insert USB cable now...
Keep "VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+ and VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+" button untill inserting USB cable.
Detected(14) : MediaTek USB Port (COM14)
[14] \\?\usb#vid_0e8d&pid_0003#5&cf6f6ce&1&4#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
CPU: MT6761 CPU code: 717 Target config: e5
***********************
Secure boot enabled: true
Need serial link authorization: false
Need download agent authorization: true
SWJTAG enabled: true
EPP_PARAM at 0x600 after EMMC_BOOT/SDMMC_BOOT: false
Root cert required: false
Memory read authorization: true
Memory write authorization: true
Cmd 0xC8 blocked: true
***********************
Executing exploit, do not disconnect phone
Exploit has been executed successfully.
[3b600]Dumping phone preloader.
Preloader: C:\GSMShield\MTK_Gsmshield_Backup_Folder\preloader _backup\preloader_k61v1_64_bsp.bin
Waiting for handle to become active......
Reseived active handle repply from phone......
Booting phone
Detected(14) : MediaTek USB Port (COM14)
[14] \\?\usb#vid_0e8d&pid_0003#5&cf6f6ce&1&4#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Boot mode: Brom
Phone detected...Please wait
BBCHIP: 6761 200 ca01
Using Algo 1.
Helio MT6761 phone detected, swithing to helio api
Helio enabled DRAM in First Da: FALSE
Sending loader.....
BBCHIP MT6761
[1]Storage EMMC
Block size: 512
EMMC FW VERSION: 00:00:00:00:00:00:00:00
EMMC CID: 90014A48414734 : 000000000000000000
EMMC UA SIZE: 0x3ab400000
BOOT STYLE: EMMC BOOT
FULL LENGTH: 0x3ac000000 [14.688 GB]
Status: USB_HIGH_SPEED
Detecting high speed port, wait......
If driver not installed, install high speed port driver.
If not need high speed port, disable it.
After repeat opperation.
Detected(20) : MediaTek DA USB VCOM (Android) (COM20)
[20] \\?\usb#vid_0e8d&pid_2001#5&cf6f6ce&1&4#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Detecting format adress....wait!
Starting generic userdata format...!
Partition: cache begin: 0x115800000 length: 0x10000000
Partition: userdata begin: 0x125800000 length: 0x2820fbe00
Phone can start slow at first power on
If phone stuck on logo, perform wipe from recovery.
First start can take up to 5 min on some phones.
[helio]Wait untill phone will start charging.
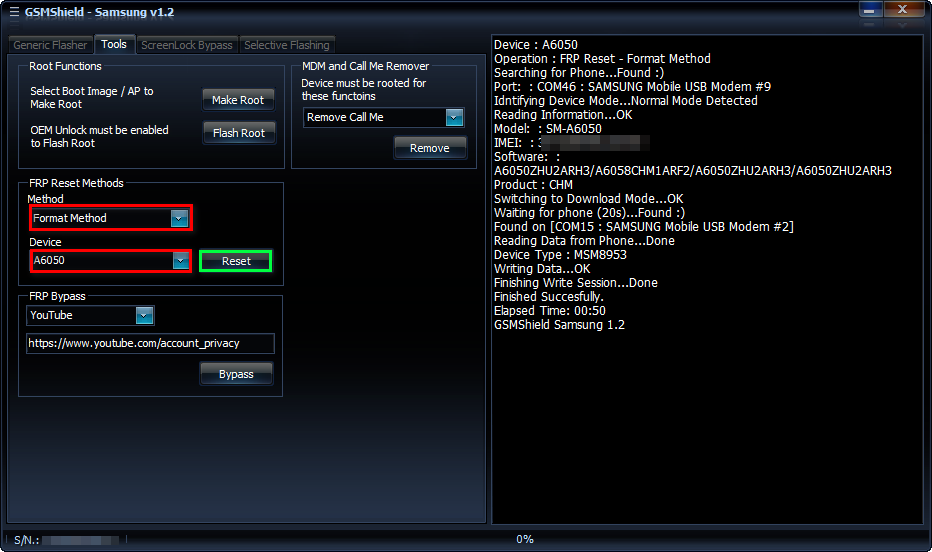
[0]All done.Huawei Y6P MED-LX9 Repair imei Done One Click By GsmShield Box
Selected connection metod: Flash Connection
Exe version: GSMSHIELD MTK 2.5
Selected phone: MT6765
Action : IMEI REPAIR.
Phone must be off with battery inside.
Battery must be charged
Please insert USB cable now...
Keep "VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+ and VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+" button untill inserting USB cable.
Detected(17) : MediaTek USB Port (COM17)
[17] \\?\usb#vid_0e8d&pid_0003#6&1c34a361&0&2#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
CPU: MT6765 CPU code: 766 Target config: e5
***********************
Secure boot enabled: true
Need serial link authorization: false
Need download agent authorization: true
SWJTAG enabled: true
EPP_PARAM at 0x600 after EMMC_BOOT/SDMMC_BOOT: false
Root cert required: false
Memory read authorization: true
Memory write authorization: true
Cmd 0xC8 blocked: true
***********************
Executing exploit, do not disconnect phone
Exploit has been executed successfully.
[3e800]Dumping phone preloader.
Preloader: C:\GSMShield\MTK_Gsmshield_Backup_Folder\preloader _backup\preloader_k62v1_64_mex_a32.bin
Waiting for handle to become active......
Reseived active handle repply from phone......
Booting phone
Detected(17) : MediaTek USB Port (COM17)
[17] \\?\usb#vid_0e8d&pid_0003#6&1c34a361&0&2#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Boot mode: Brom
Phone detected...Please wait
BBCHIP: 6765 0 ca00
Using Algo 1.
Helio MT6765 phone detected, swithing to helio api
Helio enabled DRAM in First Da: FALSE
Sending loader.....
BBCHIP MT6765
[1]Storage EMMC
Block size: 512
EMMC FW VERSION: 00:00:00:00:00:00:00:00
EMMC CID: 90014A68433861 : 000000000000000000
EMMC UA SIZE: 0xe8f800000
BOOT STYLE: EMMC BOOT
FULL LENGTH: 0xe91000000 [58.266 GB]
Status: USB_HIGH_SPEED
Detecting high speed port, wait......
If driver not installed, install high speed port driver.
If not need high speed port, disable it.
After repeat opperation.
Detected(18) : MediaTek DA USB VCOM (Android) (COM18)
[18] \\?\usb#vid_0e8d&pid_2001#6&1c34a361&0&2#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Reading imei
IMEI[1]: 86xxxxxxxxxxxx
IMEI[2]: 86xxxxxxxxxxxx
Backup saved: C:\GSMShield\MTK_Gsmshield_Backup_Folder\nvram_bac kup\FLASH_MODE_NVRAM_MT6765_xxxxxxxxxx_02_15_2023_ 20_47_34.zip
Writing imei
[helio]IMEI[1] TO UPDATE: 86222xxxxxxxxx1
[helio]IMEI[2] TO UPDATE: 86222xxxxxxxxx9
Generic IMEI OK
Writing imei in proinfo file.
Write proinfo ok.
[helio]Processing dinamic imei.
[helio]IMEI[1] TO UPDATE: 86222xxxxxxxxx1
[helio]IMEI[2] TO UPDATE: 86222xxxxxxxxx9
Write done
[helio]Wait untill phone will start charging.
[0]All done.